Domestic violence is an escalating public-health crisis that affects more than one in three women and one in four men in the United States, according to the CDC’s 2024 National Intimate Partner and Sexual Violence Survey. While every survivor’s situation is unique, one constant remains: staying connected to a trusted support network is vital — and often lifesaving. Unfortunately, abusive partners frequently monitor phones, social media, and location data, making even a simple “I’m okay” message risky.
This guide explains how discreet, automated daily check-ins can fit into a survivor-centered safety plan without drawing unwanted attention. Whether you are a survivor planning your exit, an advocate helping clients build protective strategies, or a law-enforcement agency looking to modernize welfare-check protocols, the principles below will help you leverage technology like ConfirmOk safely and effectively.
Why Daily Check-ins Matter in a Domestic Violence Safety Plan
- Rapid confirmation of safety — If a check-in window is missed, alerts allow friends, family, or authorities to intervene early.
- Reduced isolation — Automated calls or texts provide a routine touch point that an abuser can’t easily detect as a plea for help.
- Emotionally supportive — Knowing someone will notice if they don’t respond can give survivors the confidence to carry out other elements of their plan.
- Documented history — Time-stamped logs create an independent record that can corroborate future restraining-order filings or investigative needs.
Common Challenges Survivors Face With “Regular” Check-ins
- Phone surveillance: Abusers install spyware or demand unlocked access, making manual texts unsafe.
- Inconsistent schedules: Work shifts, school pickups, and unpredictable confrontations can derail fixed calling times.
- Signal loss: Rural areas or controlled Wi-Fi limit the ability to send data-heavy app pings.
- Escalation risk: If the partner discovers coded language, missed messages may trigger violence.
Automated voice calls that look like ordinary robocalls, or unobtrusive SMS prompts, help bypass many of these barriers.
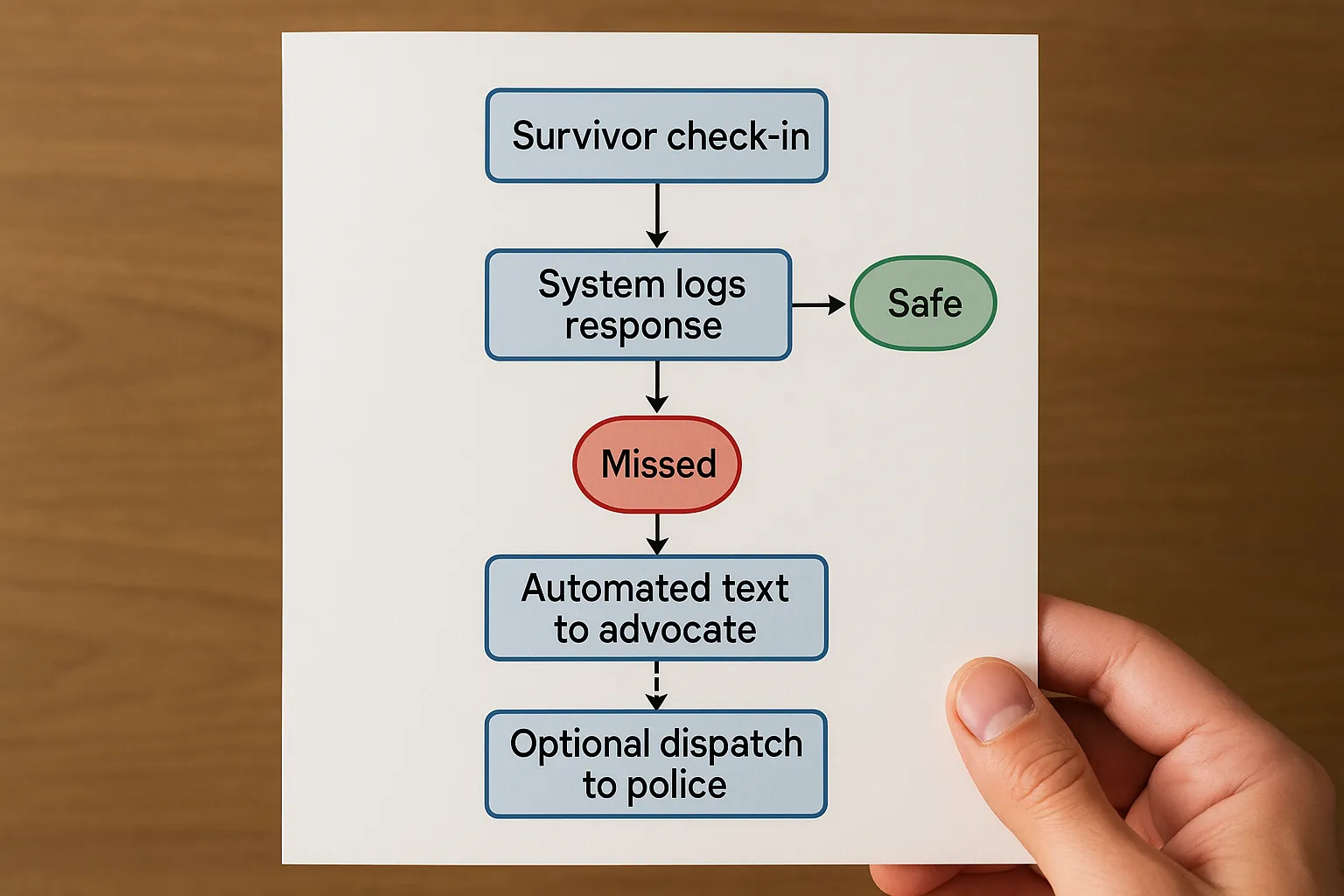
How Discreet Automated Check-ins Work
| Check-in Method | What the Survivor Sees | What the Abuser Sees | Response Time | Typical Trigger for Alerts |
|---|---|---|---|---|
| Voice call (ConfirmOk default) | A neutral caller ID. Survivor presses 1 # to confirm safety. |
A generic missed call or answered call; no message history. | < 15 seconds | No input or wrong key entry within the scheduled window |
| SMS prompt | Short text: “Your scheduled reminder: Reply ‘Y’ when convenient.” | A single, vague system text; no sensitive wording. | < 60 seconds | No “Y” reply in the allotted period |
| Passive timeout (optional) | Nothing; only used if calls go unanswered | Nothing | 2–10 minutes (configurable) | Failure to engage after multiple attempts |
Because ConfirmOk stores data on encrypted U.S.-based servers and requires no app installation, survivors avoid leaving digital footprints on shared devices.

Step-by-Step: Building a Check-in Schedule That Won’t Raise Suspicion
- Identify low-risk windows. These could be the survivor’s morning shower, a daily dog-walk, or an abuser’s regular commute.
- Vary the exact minute. Instead of 7:00 a.m. sharp, choose a 15-minute window so patterns aren’t obvious to a controller reviewing phone logs.
- Select an innocuous caller ID. ConfirmOk’s system can show an everyday toll-free number rather than words like “Wellness Check.”
- Define the care group. Survivors can add unlimited members — a neighbor, a sibling out of state, a shelter advocate, or a detective on a protective-order detail.
- Set tiered alerts. Example: If no check-in for 10 minutes, send silent SMS to the advocate; at 30 minutes, escalate to 911 dispatch (if pre-authorized by local law enforcement). Agencies using ConfirmOk’s organizational dashboard can automate that flow.
- Run a dry-run. Survivors and advocates should test the system at a safe location to ensure key presses, SMS replies, and contact numbers all work.
Integrating Check-ins With a Comprehensive Safety Plan
Automated calls are only one layer. Survivors should coordinate the following elements:
- Emergency code words with children or neighbors.
- Pre-packed “go bags” containing IDs, cash, medication, and chargers stored outside the home.
- Alternate transportation routes in case an abuser disables a vehicle.
- Legal documentation (protective orders, custody papers) kept in cloud storage and with a trusted person.
The National Domestic Violence Hotline (800-799-SAFE) provides free, confidential planning assistance and can incorporate a ConfirmOk routine into its tailored advice.
Best Practices for Advocates and Law-Enforcement Partners
- Use neutral language in all configuration fields. Avoid labels like “Danger Alert.” Even email notifications should have plain-wrap subject lines.
- Leverage flexible scheduling. Shift workers and parents juggling child-care benefit from multiple daily windows; ConfirmOk lets organizations import custom calendars in CSV format.
- Document consent protocols. Survivors must authorize any automatic 911 escalation in writing to respect privacy and prevent false dispatches.
- Train staff on trauma-informed responses. When an alarm fires, responders should prioritize survivor autonomy and immediate medical needs before evidence collection.
Real-World Scenario: “Monica” and Her Support Circle
Monica is planning to leave her emotionally abusive spouse. She works in retail, starting at 6:00 a.m., and her partner sleeps until 7:00 a.m. With her advocate, she configures ConfirmOk to call at 6:10 a.m. while she’s stocking shelves. If she presses 1 #, her sister and advocate receive a silent success log. If no response after two retries, the system sends a discreet SMS to her store manager: “Please check stockroom status.” The phrase is a pre-arranged cue to phone Monica directly and, if no answer, alert police. Monica’s partner never sees the activity because the phone log looks like spam calls from “CUSTOMER SVC.”
Within two weeks, Monica initiates her move. On departure day, she intentionally skips the call; her sister receives the alert and drives to their rendezvous point. The abuser never realizes the technology involved.
Getting Started Safely
- Open a private browser window on a device the abuser can’t access (public library, work computer, friend’s phone).
- Visit ConfirmOk.com and select “Try It Free” to create an account with only a first name and secondary email.
- Add one trusted contact and run a test call. The entire setup takes under five minutes.
- Integrate the finalized call schedule into your broader safety plan and share it only with essential allies.
If you are an advocate, shelter director, or law-enforcement agency interested in bulk licenses, contact ConfirmOk’s community-safety team for custom reporting and grant-funding guidance.
Key Takeaways
- Discreet, automated check-ins reduce surveillance risks while giving survivors rapid access to help.
- Flexible call windows, neutral caller IDs, and encrypted data storage are essential features for domestic-violence use cases.
- Coordinating alerts with trusted individuals and responders ensures missed check-ins trigger the right level of intervention.
- ConfirmOk’s no-app, no-equipment model fits seamlessly into safety plans without tipping off an abusive partner.
When every minute counts, the simplest action — pressing 1 # on a routine call — can be the difference between silent suffering and timely rescue. Secure your first discreet daily check-in today at ConfirmOk and help transform safety planning into real-time peace of mind.

